The record-breaking increase in the bandwidth of Distributed Denial of Service (DDoS) attacks (over 1Tbps for a single attack as of 2018) in recent years has finally shattered the presumption that it could be dealt with at the edge of the Enterprise network. Today’s DDoS attacks can deliver such an overwhelmingly large amount of traffic to the victim’s network that even the most capable and sophisticated traffic filtering solutions cannot save the day.
Why not? Well, we must remember what the essence of the DDoS attack is: It is to deny serviceto legitimate users of that service. An attack is considered successful not if it manages to crash a server or a service, these are merely means to an end, but rather when and if a user cannot receive the service promised. A server’s health might be perfect, the service running on it might have plenty of resources to continue its operation, yet users may still be unable to access the service.
But how? Let’s look at the network as a whole. The network is all connected, but not uniform. It can be compared to a blood vessel system in the human body: the main big arteries are the transoceanic fiber cables that carry traffic across the Tier 1. These obviously have the largest bandwidth capacity out there. Then we have smaller arteries, or Autonomous Systems, carrying traffic closer to where it needs to go. These are high bandwidth as well, though not as high as the Tier 1 bandwidth. What is important to understand though, is that eventually the traffic comes to the Data Center/Enterprise network/End User. It arrives there via network links with bandwidth comparable to that of small capillaries in our fingers. The bandwidth of the link connecting a typical DC/Enterprise to its ISP is much less than 1Tbps and as such can be fully overrun by malicious traffic. When this happens filtering the ingress traffic in the DC/Enterprise network will not help. Legitimate user’s traffic will be dropped before it enters the DC/Enterprise network due to lack of available network bandwidth.
Is there a solution? Yes, there is! Filter the incoming traffic as far away from your network as possible, where the channel bandwidth is greater! The Enterprise still needs to detect the attack on its premises and inform the ISP along with the attacker’s details. The ISP can then install policies across its network equipment to drop/re-route/shape the traffic destined to you until the threat is gone.
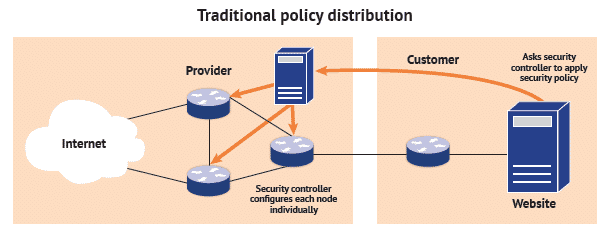
The process of applying policies across a range of network nodes, managing transactions, overcoming cross-vendor boundaries and keeping everything in sync can become rather complex. Scalability and response times are often poor, since we need a centralized controller that delivers the policies across the provider’s network.
Luckily there’s a way to overcome these challenges and provide the network with the mitigation capabilities it needs: BGP FlowSpec (RFC 5575) is a standardized mechanism for security policy distribution across the network via BGP advertisements. A Provider’s edge routers with built-in FlowSpec support can distribute the rules for dropping/re-routing/shaping precisely defined traffic within the provider’s network.
FlowSpec has the same functional set as traditionally applied mitigation measures (Remotely Triggered Black Hole, Access Control List, Policy Based Routing) but also acts in a distributed manner, rendering a centralized controller redundant. Since FlowSpec policies are distributed using BGP advertisements, there’s no longer an issue of inter-vendor operability.
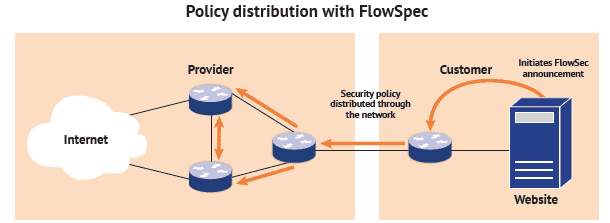
Keeping in line with today’s security needs is important, that is why we see FlowSpec being adopted by such major network equipment producers as Cisco and Juniper. We expect that ISPs favoring FlowSpec-capable devices is to follow. This technology helps make networks safer, and for us at IP Infusion this is the goal. Given our expertise in this domain, we can design a DDoS detection and protection framework containing state-of-the-art processing technologies. We also help our customers extend and improve the functionality and performance of existing Network Operating Systems (NOS).

