Docker containers are designed to be quite secure, especially if you run your processes as non-privileged users inside the container. But in order to assure you are using Docker safely, you need to be aware of the security issues and techniques for securing container-based systems.
In the first blog of the 2-part series about Docker Container Security, we highlighted cyber-criminal activities that exploited Docker containers security issues, introduced the first two tips that every enterprise should be taking into consideration when using Docker as container solution.
Here are more advanced tips to help.
Harden Docker Host with Kernel Security Features
You can add an extra layer of safety by enabling AppArmor, SELinux, GRSEC, or another appropriate hardening system provided by modern Linux kernels.
For example, you can run a kernel with GRSEC and PAX. This adds many safety checks, both at compile-time and at run-time. Alternatively, you can use AppArmor, which is a Linux security module that protects an operating system and its applications from security threats by using a security profile that can be loaded and enforced by Docker.
Vulnerability Scanning
Vulnerability scanners should be used to check that Docker images are not compromised. They provide valuable information about potential security vulnerabilities and allow you to choose images that align with enterprise security standards. Docker offers a security scanning tool in its EE (Enterprise Edition), and each of the images in the Official Images is scanned for vulnerabilities. Also, there are several cloud companies that offers a Cloud Private Docker Registry with vulnerability scanning features.
Vulnerability scanners should be a mandatory and automatic step of CI/CD platforms. Just manually checking the images now and then, or just as the final step when the built Docker image is stored in a private Docker Registry is risky.
Limit Docker Privileges
Docker should not be run privileged mode (i.e., “-privileged”). Docker does not, by default, run containers as privileged. If specific capabilities are required for a container, grant only those capabilities. If you have ensured the safety and authenticity of the source (as discussed above) this issue is less important, but nonetheless, good practice.
Also, containers should always run as non-root users. Create a user with a known uid, set it in the Dockerfile, and run the application process using it. The same thing can be done with a gid. Tools can be used to run the CMD command with a preset UID and GID.
Finally, avoid mounting /var/run/docker.sock. This is a very dangerous practice since the Docker engine runs as root and has access to the host.
Docker Runtime Monitoring
Implementing a monitoring and alerting operation is important. You need to actively monitor your application to detect, and alert about anomalous, suspicious, and malicious container behaviors.
There are several available open-source tools can be used to build a monitoring and alerting operations. Some of these tools emphasize behavioral monitoring for containers, hosts, and network activities to detect anomalies and set up alerts for any type of Linux system calls. Other tools collect/receive/store metrics and expose them in graphs.
Docker provides stats where you can check current memory usage and limits, but since it does not store any data, it is not enough to ensure proper and secure operation.
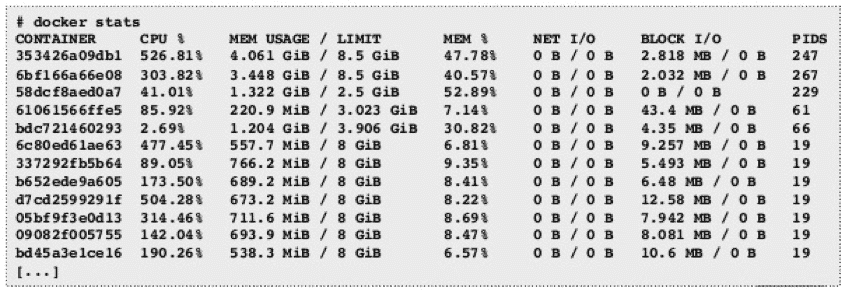
Besides Docker stats, we can use cAdvisor, a monitoring tool for Docker containers offered by Google. It consists of a single container. It is accessed via a graphical interface and shows statistics for containerized applications.
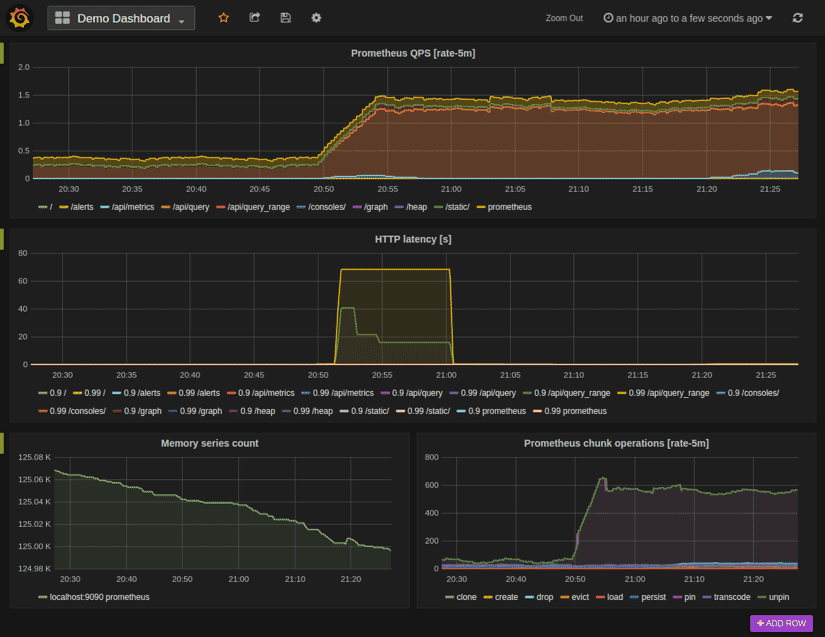
And another important monitoring tool for Docker containers is Prometheus, an open source toolkit used for monitoring and alerting. You can configure Docker as a Prometheus target, and in conjunction with Grafana, it provides a powerful monitoring system that can be used to monitor containers and alert Ops teams about the health of the environment.
At IP Infusion, we strongly advise and guide our customers to follow the best security practices while implementing container solutions in their products.

